
CAS Overview
CAS partners with a Financial Agent and Merchant Processor to provide merchant services to our federal agencies. Through the success of this partnership, CAS is able to offer payment card processing through a half-dozen acceptance points and provide a robust portfolio of products and services such as: Europay, MasterCard & Visa (EMV), End-2-End Encryption, Near-Field Communication and Tokenization. The CAS footprint continues to grow as the program processes at approximately 10,000 locations over 19,000 point-of-sale endpoints.
How CAS Works
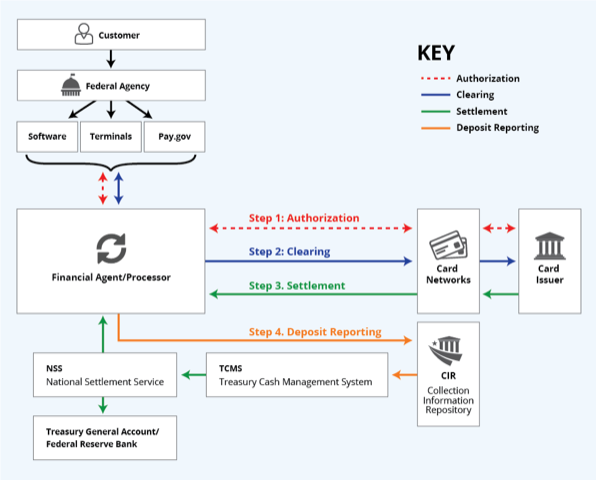
Existing Card Acquiring Service Operations are Extensive and Complex. Processing payment card transactions typically involves two primary stages:
- Transaction authorization, where a payment request initiated with a card account is sent electronically through various parties in the payment card ecosystem (i.e., from the accepting merchant/agency to the acquirer/processor, and routed through the card network to the issuing bank), with an approval or decline message returned back to the acceptance point; and,
- Clearing and settlement, where card transactions are reconciled with the acquirer/ processor, routed via the card networks and settled against issuing and acquiring accounts. CAS card transactions are accepted throughout the day, with next day funds availability. Transactions settle to the Treasury’s account at the Federal Reserve prior to 2:00 pm ET for the prior day’s transactions.
The diagram below demonstrates the payment card processing from authorization (red) through clearing and settlement (blue and green, respectively).
Card Acquiring Service 101
This presentation introduces the CAS program, it’s history, and how to get enrolled.
